What concerns you most about your conference calls? Call quality and reliability? The success of your meetings?
What about having someone snoop on your call?
With Zoom-bombings highlighting the needs of security across conferencing platforms, we want to draw attention to the importance of security – even during your conference calls.
Over the past two and a half decades, audio conferencing has changed significantly. The primary change has revolved around the development of software that utilizes web-based protocols and applications to control and carry conference calls better. (Your friends here at MeetingOne were some of the pioneers in this field of “internet-enhanced conferencing”!)
Why is security important again? Even before the coronavirus forced everyone to work from home, more meetings were being held across the world than ever before. One estimate places the number around 11 million per day – in the US alone! With the rise of COVID-19, millions more meetings are being held over the phone or web. More meetings, greater potential exposure to threats.
It’s likely this trend will continue even after things return to normal.
What’s worse is the simple fact that call hosts often don’t know who is on their call. A 2015 LoopUp survey found 99% of the respondents couldn’t say they always knew who was on their calls. Of those same call hosts, 93% said they occasionally shared confidential information during meetings.
What does that mean? Well, many call hosts are sharing sensitive information during calls – but they have no clue with whom they are sharing it!
As an excellent case in point, in 2012 the FBI held a conference call with Scotland Yard. Their topic: How to handle hacktivists. (Hacktivists are individuals who hack entities, for social or moral reasons, they believe to be corrupt.) Lo and behold, one such hacktivist snuck onto the call and posted the recording on the internet! Talk about irony.
To help you make the best assessment of your overall teleconferencing security, we’re following up our previous blog, “6 Factors of Web Conferencing Security You Need to Consider,” with a discussion on audio conferencing security.
(If you’d like to see the full picture of all the factors shaping into secure conferencing, download our easy to read whitepaper!)
Threats to Your Audio Conferencing Security
What are the specific threats to your conference calls? Well, there are many. Here are a few.
Call Snooping: As with web conferencing, the last thing you want is some random outsider listening in on your conference calls. Call snoopers try to find unsecured dial-in numbers for conference calls they can join. Sometimes this entails stealing information to sneak into calls. Other times call snoopers use various strategies to dial conference numbers hoping they get lucky.
In Healthcare, snooping can lead to compliance issues with HIPAA, as the confidentiality of your patients’ protected information can be compromised. Fail to comply with HIPAA, and you could be slapped with a huge fine.
For a legal firm, if someone intrudes upon your call, they could potentially damage your case and reputation – oh, and you could get sued!
Internal Leaks: When it comes to information security, internal leaks represent one of the most prevalent issues and threats. Despite everyone’s best efforts to encourage comfortable and open work environments, the occasional disgruntled employee is liable to leak information about valuable business assets, acquired during a conference call.
That said, not every leak is the result of ill intentions.
All it takes is one careless employee, who was not supposed to be on a call, to confide a vital trade-secret to the wrong person, and your business could suffer a crippled reputation and incur financial damages.
There’s a lot you are up against, so let’s get you up to speed on conference call security musts. Conferencing providers that are concerned about security will offer a range of features and functions that secure your calls.
We’ve identified 5 groups of features or factors that are critical to sensitive organizations. Read about them below.
Audio Conferencing Security: 5 Critical Factors
Factor #1: Securing Access
In the new era of audio conferencing, internet enhancement helps make for more productive meetings, through the use of features that manage group interactions. These same components can double as security elements, particularly when you are Securing Access to a conference room. Two examples of securing access are setting Conference Parameters and utilizing Access Mode Features.
- Conference Parameters: Conference parameters are broad configurations made to a conference room before the actual event. Establishing parameters, such as maximum numbers of participants, sub-conference rooms, and inactive time, help you keep track of participant movement. Parameters can also be extended to setting In-Call Default features, such as conference locks, which bar entrance to the conference once the meeting has begun.
- Access Modes: Access modes can be defined as the features regulating access into a conference room. Similar to airport security (minus the uncomfortable pat-downs), a basic access mode is Screening, where a Host can let in participants one-by-one. Or a host can merely leave the conference room locked, accessible to a participant only when they are dialed-out to by that host. (See “Factor 4: Visual Interface” for more on “dialing-out.”)
As a few more options include using specific conference codes or individual access codes to gain access. More on these below, as well.
Securing the access features of a conference room is a critical starting place for all audio conferencing security.
 Factor #2: Defining Audio Roles & Privileges
Factor #2: Defining Audio Roles & Privileges
Determining how individuals gain access to your conference rooms is of the utmost importance. To ensure individuals have the appropriate access to your conferences, you need an audio conferencing platform that makes user authentication a significant aspect for conference access. Many of the better platforms offer Contact List or Directory features, which can be used to assign the roles and privileges that will define one’s access to audio conference rooms.
Contact List or Directory: Many audio conferencing platforms use a virtual Contact List or Directory feature to define audio roles and privileges. These features serve two functions: on one side, they act as a virtual repository for your contacts; on the other, they are essential for defining an individual’s access to your room.
Better Contact List or Directory features allow you to create unique identifiers for participants that pre-approve how they can interact in your audio conference rooms. In doing so, you can keep your employee, Joe Shmoe, out of conferences he’s not supposed to attend.
Make sure to discuss with your audio provider what features they have for defining roles and privileges, and how to access these options. Defining the roles and privileges for your conferences is often the best way to prevent snooping.
Factor #3: PINs, IACs & RACs
There’s an unfortunate but very real fact: Anyone can get a conference phone number. That individual can then sneak into your conference calls. To prevent these potential break-ins, it is important your conference call provider offers Personal Identification Numbers (PINs), Individual Access Codes, and Conference Codes as standard features.
- Personal Identification Numbers (PINs) for Host: As the title suggests, a Personal Identification Number is a unique identifier provided to a host alone. Functioning as the key to unlocking audio conference rooms, PINs assure only hosts have access to and management of their rooms.
- Individual Access Codes (IACs): IACs are a rare security feature you’ll find with only a few providers. An IAC serves two roles. The first is a unique identifier for individuals. Anytime they call in and enter that specific code, they are automatically identified by the providers’ bridge and system.
The second role is as a security feature. Audio Rooms can be gated so only IACs can be used to enter. Given IACs are so unique, it limits who can join a call.
Think of IACs as fingerprints. In the same way a fingerprint scanner grants you access to a secured room, an IAC opens the door to a conference call.
- Room Access Codes (RACs): Designated by the host of a conference room, a Room Access Code is a set of numbers that provides the participants a unique entrance passcode to the respective audio conference room. These codes can also be individualized, providing each participant a personalized key to enter a conference room.
Providing conference codes is likely the most crucial step in preparing the security of an audio conference. Using codes helps limit two potential threats: outside conference hackers, and unwanted internal leaks.
Factor #4: In-Call Features
To this point, we’ve focused on the security options you should have available for managing the configuration of your audio conferences. But what are the features you need to keep an audio conference secure once it has begun? Here are a few beneficial components:
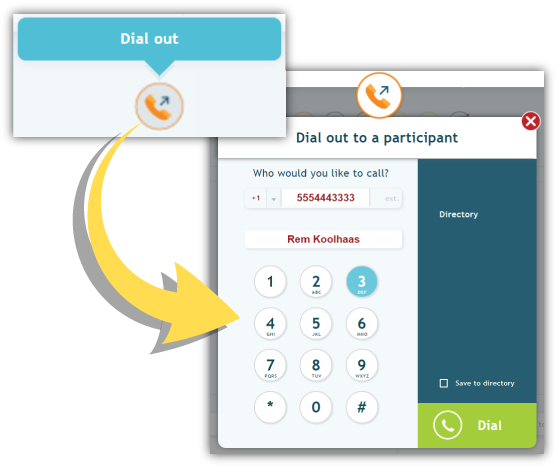
- Host Dial-Out: Perhaps you are wary that conference codes won’t suffice, and you’d rather wholly control attendee admittance yourself. Very wise. With a Host Dial-out feature, you (the host) can select and contact whom will enter your conference room, and when. This can only be done once you have started your call. And it’s much easier if you have a visual interface that allows you to use a virtual directory to select and dial contacts.
(One of the industry’s first online visual interfaces was MeetingOne’s Click&Meet. We weren’t kidding about being pioneers. The screenshots below show examples of the Click&Meet interface.)
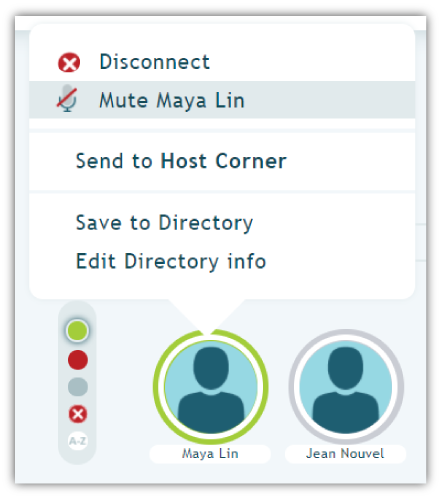
- Roll-Call: Even if you are already leveraging access modes like Screening, you may still want to double check on who has entered. To do so, utilize a conference “Roll-Call.” A roll-call feature will require attendees to record their name before entering. As attendees enter, their names will then be listed aloud. If “Jim Beam” is announced, and there’s no Mr. Beam in your workplace, you may want to dump them from the call (more on disconnecting participants below). Roll-calls can also be recorded, which provides you the option to review the names of participants after the conference.
- Muting: Muting is pretty self-explanatory, but it has significant ramifications. Imagine a situation where a team member of yours is rattling off a little too much information. Rather than let them continue, you can mute their phone. In doing so, you can avoid a leak of valuable information.
Although you can mute everyone with dial pad commands, selecting and muting a single person requires an online visual interface. Make sure your audio provider offers such software.
- Impromptu “Apparte”: French for, “Uh oh, Joe Schmoe isn’t supposed to hear this – move him out quick!” an apparte feature is a virtual space where you can place people who have been whisked away from the main conference room, spur of the moment (thus the “impromptu” aspect). Typically, you would isolate a participant in this way if they were not privy to confidential information during a conference.
As an example, Click&Meet’s Sub-Conference Rooms feature functions for impromptu apparte. Individuals can be quickly selected by a host and moved into a sub-conference room where they can’t listen in on the conversation.
(If you’d like to learn more about Click&Meet, check out this page!)
- Disconnection: To manage any instance in which you feel an unwanted guest has intruded upon your call, you need a disconnection feature. Although most audio conferencing platforms offer straightforward means to disconnect everyone from a call, only a system with an online visual interface has the functionality to disengage particular attendees.
These five features, among others, help you remove those unwanted participants or the cunning perpetrators who may sneak past the first, second, and third walls of protection.
Factor #5: Recordings
Can’t remember all that was discussed in your last conference call? With the right audio conferencing provider, call recordings can be easily acquired. Many businesses share their recordings with absent employees, trainees, and partners, so they can be aware of what was discussed during the event. In a more recent development, doctors have been recording sessions with patients, so their conversations can be later accessed by either party. The benefits of recordings are endless.
Minimally, you need to make sure any recordings your audio provider stores for you are protected while at rest, or in transit, using encryption combinations. The best methods layer symmetric and asymmetric encryptions.
With symmetric encryption, a single code is used to encrypt the data of a recording by your audio provider; then that same key is used to decipher the coded data by you. That code word, or “key,” is a secret, shared only with your provider and you for access to a recording.
Asymmetric encryption employs keys in a slightly different manner. With asymmetric encryption, you take advantage of two keys: one public, one private. Being public, one key is shared between anyone who might need it. The private key is yours alone.
Layering encryption in this way increases computational complexity, which means it’s nearly impossible for some hacker to guess the code and steal your recording.
Overall, bundling symmetric and asymmetric methods of encryption is a must for audio conferencing security.
The Right Provider for Secure Conference Calls
Getting the most out of audio conferencing technology comes when you have the assurance of safety and security. When you can worry less about managing external threats and internal leaks, it gives you the opportunity to focus on the success of your presentations and conferences.
Assessing the security features your audio conferencing provider offers is critical. Over the last few decades, MeetingOne has invested a considerable amount of time and energy into refining its audio conferencing security. Numerous organizations, both public and private, depend upon MeetingOne’s security to facilitate large-scale and daily conference calls.
We love sharing our expertise; ask how we can help ensure your audio conferencing security is up to your industry’s standards! Or check out the overview of our security features.
This blog was originally published in June of 2016; then republished on February 27, 2020.